MASTG-TOOL-0040: MobSF for iOS
By running MobSF locally on a macOS host you'll benefit from a slightly better class-dump output.
Once you have MobSF up and running you can open it in your browser by navigating to http://127.0.0.1:8000. Simply drag the IPA you want to analyze into the upload area and MobSF will start its job.
After MobSF is done with its analysis, you will receive a one-page overview of all the tests that were executed. The page is split up into multiple sections giving some first hints on the attack surface of the application.
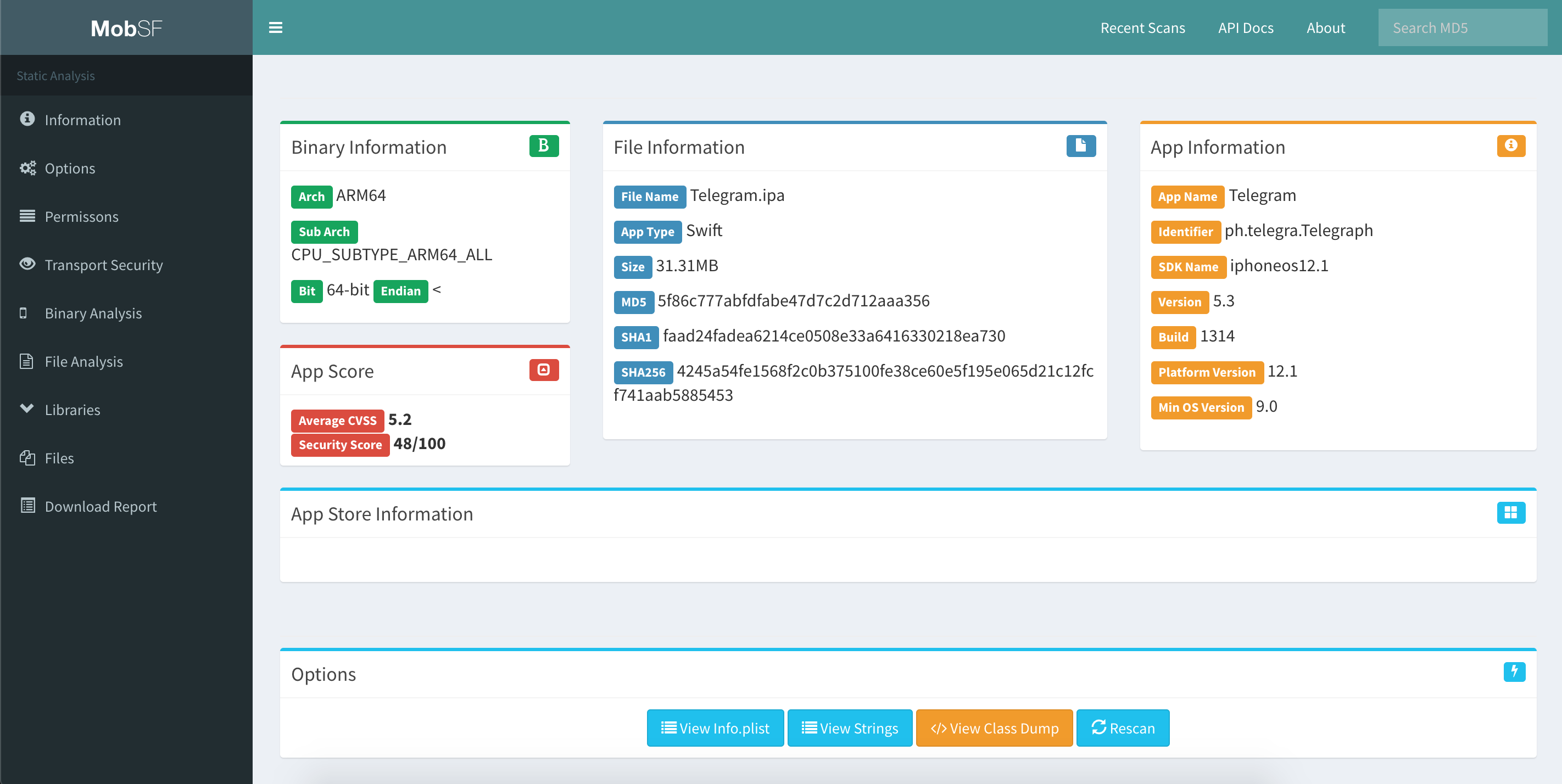
The following is displayed:
- Basic information about the app and its binary file.
- Some options to:
- View the
Info.plistfile. - View the strings contained in the app binary.
- Download a class-dump, if the app was written in Objective-C; if it is written in Swift no class-dump can be created.
- View the
- List all Purpose Strings extracted from the
Info.plistwhich give some hints on the app's permissions. - Exceptions in the App Transport Security (ATS) configuration will be listed.
- A brief binary analysis showing if free binary security features are activated or e.g. if the binary makes use of banned APIs.
- List of libraries used by the app binary and list of all files inside the unzipped IPA.
In contrast to the Android use case, MobSF does not offer any dynamic analysis features for iOS apps.
Refer to MobSF documentation for more details.